Troubleshooting: Securely Connecting Remote IoT To AWS VPC Not Working On Windows
Why is Securely Connecting Remote IoT to AWS VPC Not Working on Windows?
The reason why securely connecting remote IoT devices to an AWS VPC might not work on Windows can be multifaceted, often a combination of factors. This is a common challenge faced by developers, IT professionals, and IoT enthusiasts who rely on AWS for their cloud infrastructure. Understanding the potential culprits is the first step towards a solution. Amazon Web Services (AWS) Virtual Private Cloud (VPC) offers a robust solution for this, providing a secure and isolated environment for your IoT devices to communicate. However, the path to achieving this secure connection is not always smooth. Users frequently encounter challenges, especially when working within the Windows operating system. These challenges typically stem from: * **Misconfigurations:** Incorrectly set up security groups, network ACLs, routing tables, or VPC endpoints. * **Windows-Specific Issues:** Firewall blocks, proxy settings, DNS resolution problems, or network adapter misconfigurations on the Windows machine itself. * **IoT Core Policy and Certificate Problems:** Incorrectly defined IoT policies, expired certificates, or misattached certificates. * **Device SDK/Client Issues:** Problems with the IoT device's software client, SDK, or the way it's configured to connect. * **Network Glitches:** Underlying network connectivity issues between the IoT device and the AWS VPC. Troubleshooting "securely connect remote IoT VPC AWS not working on Windows" requires a methodical approach. The key is understanding the interplay of these components and isolating the source of the issue. Remember, each component contributes to the overall functionality.Understanding the AWS IoT VPC Landscape
Before diving into troubleshooting, it's essential to grasp the core components involved in securely connecting IoT devices to an AWS VPC. * **AWS VPC:** A logically isolated section of the AWS Cloud where you can launch AWS resources in a virtual network that you define. It gives you complete control over your virtual networking environment, including selection of your own IP address range, creation of subnets, and configuration of route tables and network gateways. * **AWS IoT Core:** A managed cloud service that lets connected devices easily and securely interact with cloud applications and other devices. IoT Core supports various protocols like MQTT, HTTPS, and LoRaWAN. * **VPC Endpoints:** These enable you to privately connect your VPC to supported AWS services and VPC endpoint services powered by PrivateLink without requiring an internet gateway, NAT device, VPN connection, or AWS Direct Connect connection. For IoT, this is crucial for secure, private communication. * **Interface Endpoints:** Powered by AWS PrivateLink, these allow you to connect to IoT Core data plane endpoints (e.g., `data.iot.region.amazonaws.com`) directly from your VPC using private IP addresses. * **Gateway Endpoints:** Used for services like S3 and DynamoDB, which might be part of your IoT data flow but are less directly involved in the device-to-cloud connection itself. * **Security Groups & Network ACLs:** Act as virtual firewalls to control inbound and outbound traffic to instances (Security Groups) or subnets (Network ACLs) within your VPC. * **Route Tables:** Control where network traffic from your subnets or gateway goes.Common Culprits & Troubleshooting Steps
Now, let's explore the common reasons for connectivity failures and how to systematically address them.1. Security Groups and Network ACLs Misconfigurations
These are often the first place to look. Even a single incorrect rule can block all traffic. * **Check Security Group Rules:** * **Inbound Rules:** Ensure that the security group associated with your VPC endpoint (if using one) or the network interface your IoT device is trying to reach allows inbound traffic on the correct ports (e.g., 8883 for MQTT, 443 for HTTPS) from the IP range of your IoT devices or the subnet they reside in. * **Outbound Rules:** Verify that your IoT device's security group allows outbound traffic to the AWS IoT Core endpoint IP range or the VPC endpoint. * **Check Network ACLs:** * Network ACLs are stateless, meaning you need to explicitly allow both inbound and outbound traffic. * Ensure rules permit traffic on the necessary ports (8883, 443) in both directions for the subnets involved. * Remember, NACLs apply to the entire subnet, not just individual instances.2. Routing Table Issues
Incorrect routing can prevent your IoT device's traffic from reaching the AWS IoT Core endpoint or VPC endpoint. * **Verify Route Tables:** * If using a VPC endpoint, ensure the route table associated with your IoT device's subnet has a route to the VPC endpoint. This typically involves a local route if the endpoint is in the same VPC. * If your IoT device is connecting via the internet (less secure, but sometimes used for initial testing), ensure your subnet has a route to an Internet Gateway (IGW). * Confirm there are no overlapping CIDR blocks that could cause routing conflicts.3. VPC Endpoints (Interface & Gateway) Problems
VPC endpoints are critical for private, secure IoT connectivity. * **Endpoint Creation and Status:** * Confirm the VPC endpoint for AWS IoT Core (Interface Endpoint) has been created successfully and is in the `Available` state. * Ensure it's created in the correct VPC and subnets where your IoT devices reside or can route to. * **Endpoint Policies:** * Review the VPC endpoint policy. It might be overly restrictive, preventing your IoT devices from connecting or performing actions. Ensure it allows `iot:*` actions or specific actions like `iot:Connect`, `iot:Publish`, `iot:Subscribe` from the necessary IAM roles or users. * **DNS Resolution:** * If you're using a VPC endpoint, ensure that DNS resolution for the IoT Core endpoint (`data.iot.region.amazonaws.com`) resolves to the private IP addresses of your VPC endpoint ENIs. * Within your VPC, ensure "DNS Hostnames" and "DNS Resolution" are enabled in your VPC settings. * On your Windows machine, verify that it can resolve the IoT Core endpoint. You can use `nslookup` or `dig` (if installed) to check.4. Device-Side Configuration (Windows Specific Nuances)
The Windows operating system can introduce its own set of challenges. * **Windows Firewall:** * This is a common culprit. Ensure Windows Defender Firewall (or any third-party firewall) on your Windows machine is not blocking outbound connections on port 8883 (MQTT) or 443 (HTTPS) to the AWS IoT Core endpoint or VPC endpoint. * Temporarily disabling the firewall (for testing purposes only, re-enable immediately after) can help diagnose if it's the issue. * **Proxy Settings:** * If your Windows machine is behind a corporate proxy, your IoT client or SDK might need to be configured to use it. Incorrect proxy settings can prevent outbound connections. * Check system-wide proxy settings in Windows (Settings > Network & Internet > Proxy). * **Network Adapter Settings:** * Verify the network adapter settings on your Windows machine (IP address, subnet mask, default gateway, DNS servers). Ensure they are correctly configured to reach your VPC or the internet. * **DNS Resolution on Windows:** * Beyond the VPC DNS settings, ensure your Windows machine itself is using DNS servers that can correctly resolve the AWS IoT Core endpoint. If using a VPC endpoint, this typically means using the VPC's default DNS resolver. * **IoT Device SDK/Client Configuration:** * **Endpoint:** Double-check that the IoT client or SDK running on Windows is configured with the correct AWS IoT Core endpoint (e.g., `a1234567890abc.iot.us-east-1.amazonaws.com`). If using a VPC endpoint, ensure it's configured to use the private endpoint URL if your SDK supports it, or that DNS resolution correctly points to the private IPs. * **Certificates and Private Key:** Ensure the correct device certificate, private key, and root CA certificate are present, valid, and correctly referenced by your IoT client. Incorrect or expired certificates are a very common reason for connection failures. * **Time Synchronization:** Devices with incorrect system time can fail certificate validation. Ensure your Windows system's clock is synchronized.5. AWS IoT Core Policies and Certificates
Even if network connectivity is perfect, incorrect AWS IoT Core configurations will prevent connection. * **IoT Policy Permissions:** * Review the IoT policy attached to your device's certificate. It must grant the necessary permissions for `iot:Connect`, `iot:Publish`, `iot:Subscribe`, and `iot:Receive` on the appropriate topics. * Ensure the policy's `Resource` ARN is correct (e.g., `arn:aws:iot:region:account-id:client/${iot:ClientId}` for `iot:Connect`). * **Certificate Attachment:** * Verify that the device certificate used by your IoT client is correctly attached to the IoT Thing and has the necessary IoT policy attached to it. * **Certificate Status:** * Confirm that the certificate status in AWS IoT Core is `ACTIVE`. If it's `INACTIVE` or `REVOKED`, the device won't connect.6. Logging and Monitoring
Effective troubleshooting relies heavily on good diagnostics. * **AWS CloudWatch Logs:** * Enable CloudWatch logging for AWS IoT Core. This can provide valuable insights into why connections are failing (e.g., "TLS Handshake Failed," "Policy Denied"). * Monitor VPC Flow Logs: If enabled for your VPC, Flow Logs can show if traffic from your IoT device is reaching your VPC endpoint or IoT Core, and if it's being accepted or rejected. This helps pinpoint network-level issues. * **Windows Event Viewer:** * Check Windows Event Viewer for any network-related errors, firewall blocks, or application-specific issues that might indicate why your IoT client isn't connecting. * **IoT Client Logs:** * Configure your IoT device's client application or SDK to output detailed logs. These logs are often the most direct way to see connection attempts, errors, and reasons for failure from the device's perspective. Look for specific error codes or messages.Best Practices for Secure IoT VPC Connectivity
Once you've resolved your immediate issues, consider these best practices to prevent future problems and maintain a robust, secure IoT ecosystem: * **Principle of Least Privilege:** Grant only the necessary permissions in your IoT policies and security groups. Avoid overly broad rules (e.g., allowing `0.0.0.0/0` inbound traffic unless absolutely necessary and justified). * **Infrastructure as Code (IaC):** Use tools like AWS CloudFormation or Terraform to define your VPC, subnets, security groups, VPC endpoints, and IoT Core resources. This ensures consistency, reduces manual errors, and makes it easier to replicate or audit your setup. * **Regular Audits:** Periodically review your security groups, network ACLs, routing tables, and IoT policies to ensure they align with your security posture and current requirements. * **Dedicated VPC Endpoints:** Always use VPC Interface Endpoints for private connectivity to AWS IoT Core data plane endpoints. This enhances security by keeping traffic within the AWS network. * **Version Control:** Keep your IoT device code, certificates, and configuration files under version control. * **Thorough Testing:** Implement a robust testing strategy that includes unit tests, integration tests, and end-to-end connectivity tests to validate your setup.Conclusion
Connecting remote IoT devices to an AWS VPC securely is a fundamental requirement for many modern applications. While encountering issues such as "securely connect remote IoT VPC AWS not working on Windows" can be frustrating and disruptive, it's a solvable problem. This comprehensive guide has equipped you with the actionable steps, insights, and best practices necessary to ensure a secure and reliable connection between your remote IoT devices and your AWS infrastructure. By systematically troubleshooting security groups, routing tables, VPC endpoints, and especially device-side Windows configurations, you can pinpoint and resolve the underlying causes of connectivity failures. Remember, each component contributes to the overall functionality, and a methodical approach, combined with diligent logging and monitoring, is your best ally. Mastering secure connectivity ensures your IoT ecosystem runs smoothly, securely, and efficiently, whether you're a seasoned pro or just starting out.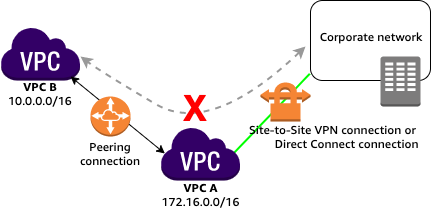
Unsupported VPC peering configurations - Amazon Virtual Private Cloud
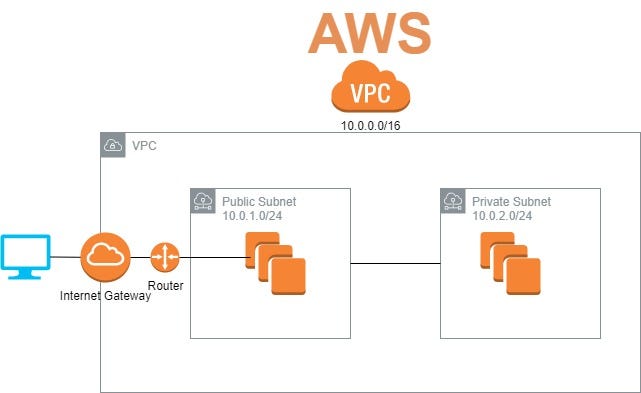
AWS Custom VPC. I wanted to launch & connect my EC2… | by Naveen Singh
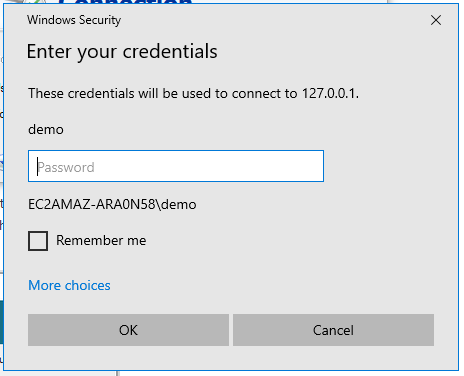
Making a Remote Desktop connection to the AWS Guest VPC – remote.it